
- Check Point Research Publications
- Threat Research
Research by Itay Cohen from Check Point Research and Omri Ben Bassat from Intezer This research is a ...
- Check Point Research Publications

Research By : Mark Lechtik & Nadav Grossman Introduction Earlier this year, our colleagues ...
- Check Point Research Publications

Research By: Artyom Skrobov, Slava Makkaveev Introduction Check Point Researchers have identified a ...
- Check Point Research Publications
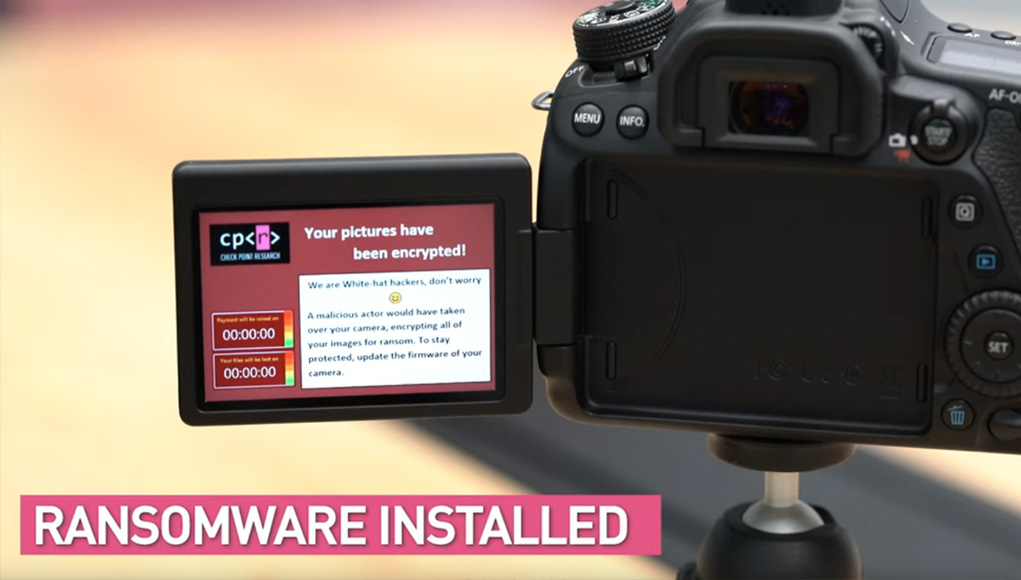
Research by: Eyal Itkin TL;DR Cameras. We take them to every important life event, we bring them on our ...
- Check Point Research Publications

Gaining code execution using a malicious SQLite database Research By: Omer Gull tl;dr SQLite is one of the ...
- Check Point Research Publications

Research By: Dikla Barda, Roman Zaikin and Oded Vanunu According to sources , WhatsApp, the ...
- Check Point Research Publications

Research by: Eyal Itkin Overview Earlier this year, we published our research on the Reverse RDP Attack . In ...



