
- Check Point Research Publications

Research by: Eran Vaknin and Alon Boxiner The goal of Microsoft Management Console (MMC) is to ...
- Check Point Research Publications
- Threat Research

Research by: Ronen Shustin Introduction About a year ago Check Point Research discovered ...
- Check Point Research Publications

Research by: Ben Herzog It's possible to write any program in any programming language; that's what ...
- Android Malware
- Check Point Research Publications
- Threat Research

Earlier today the Financial Times published that there is a critical vulnerability in the ...
- Check Point Research Publications

Check Point researchers have carried out an investigative research that allows for a rare opportunity of ...
- Check Point Research Publications
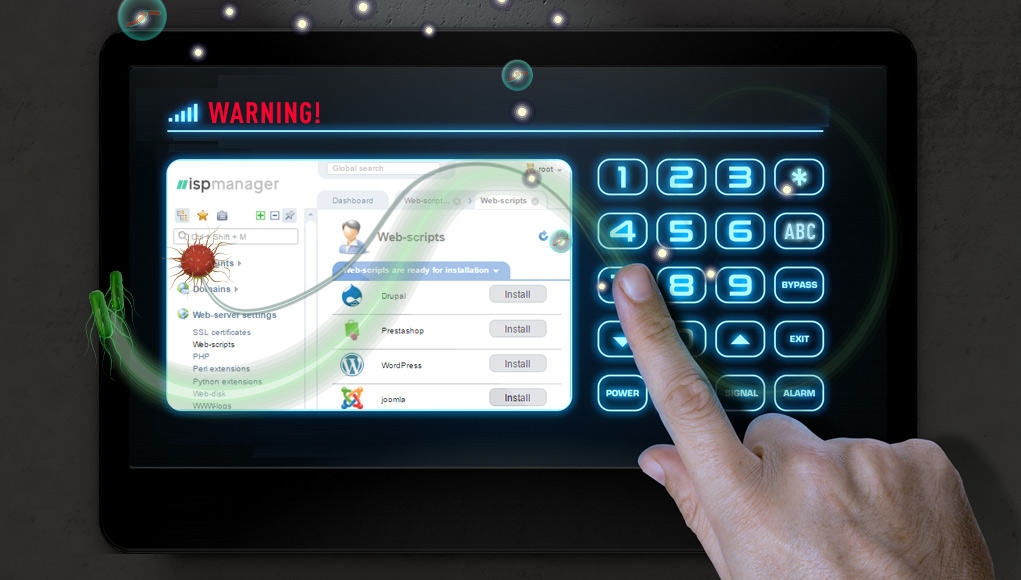
Research by: Alexey Bukheyev and Aliaksandr Chailytko ISPsystem panel is a well-known software with ...
- Check Point Research Publications

Research by: Itay Cohen @import ...
- Check Point Research Publications

Introduction Recently, Check Point researchers spotted a targeted attack against officials within ...


